What is Out-of-Band, or OoB?
Wikipedia defines Out-of-Band as "communication by other than the normal communication method". Ok, what the hell does that mean, then?
In essence, it means any communication method that is different from the primary method we're interested in, like a phone call or text message when the primary method is the Internet. And just so you know, in this article we're mainly concerned with Out-of-Band authentication, specifically multi-factor authentication.
So let's say that you're signing into your bank website. While you're signing in, a keylogger your computer was infected with through a 'drive-by' download attack captures your password and relays it to a hacker. You're finished. But wait! Your bank has additional security questions to ask you. Oh, hang on... the keylogger is going to get the answers to those, too, and if not, it's probably going to be something like your mother's maiden name, your high school mascot, or a previous address. If you answered these questions truthfully (which you shouldn't do), that information is easily found online, either on the dark-web, or even on certain clearnet sites for $0.95! Yes, that's right folks for the low low price of only 95 cents, you too can answer many personal questions on behalf of someone else.
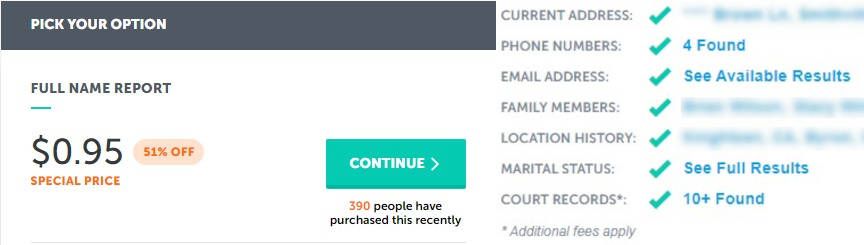
That is an example of all authentication steps being "in-band", and in the case of a compromised system, it is very ineffectual. What you need is something outside of the online channel.
Enter Two-factor Authentication (2FA)
What could save you in the case above is if your bank offered 2-factor authentication and you've activated it. A 2nd factor is something you have (phone or a USB key) or something you are (fingerprint, face, etc.) in ADDITION to the something you know (password). Many companies either don't offer true OoB 2FA, or offer a really easy way to bypass it for the sake of convenience, but more on that later.
Here are some common examples of 2FA methods:
- A one-time PIN (OTP) code texted to your mobile phone
- A similar code sent in an email
- A code generated by a time-based one-time PIN (TOTP) app on your phone or on a hardware token
- A secure code generated by a USB or NFC-based hardware token
Some of these methods are great, one is OK, and one is not out-of-band at all. Can you spot that one?
Emailed codes may seem like they are a good solution. But in our example of a compromised system with a keylogger on it, it's easy to get your Email password too. Or, a determined hacker would be able to sniff your traffic and grab that code before you do, since most email is transmitted in the clear (I'll have a future article about that and how you can protect your Email).
Well, then. A code sent by SMS. That seems good. That actually is out-of-band. It's not using the Internet (well it is, but that's in your carrier's back-end systems and encrypted). Banks and other companies love SMS as a second factor because of the ubiquity and familiarity of mobile phones among their customers.
But wait... There are problems with that too, unfortunately. There is a technique that a hacker can use called SIM swap. It isn't easy - it's unlikely to happen to you, but it is possible, especially if your mobile carrier has been hacked. A skilled hacker can easily use social engineering to psychologically manipulate an employee of your carrier into porting your phone number over to a phone that the hacker controls, without you even knowing. Again, most of the personal information needed to verify your identity to your carrier is readily available online (especially if your carrier was the victim of a data breach).
OK, so what are we left with, then?
Where OoB authentication shines
Here is where having a second factor that is TRULY out-of-band is key. And it should not be accessible by the same means as the website you're logging into, and shouldn't be easily taken over.
Many large companies have employees who work remotely log into internal systems using a hardware or hard token which generates a new code once every minute or once every 30 seconds.
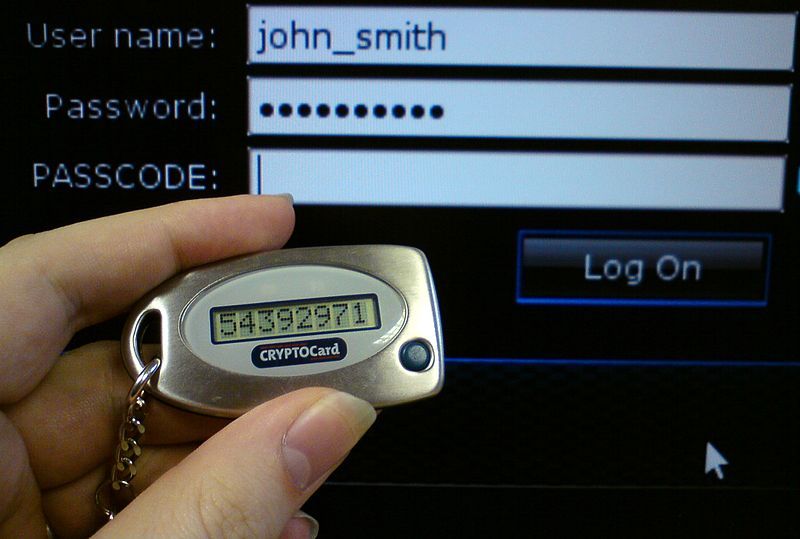
These are great. It is just about as far out-of-band as you can get from the Internet without using paper codes. It can be expensive though, and they're not really widely supported by regular sites.
A great alternative is a FIDO2 compliant hardware device like a Yubikey or Google Titan Key, which works via USB or NFC to generate a secure code directly in software, and without using the keyboard or clipboard.

If your bank offers it, you should set up a 2nd factor using something like this. Sadly most don't support this method. Not yet. It is expensive for them to implement, and it can be inconvenient for customers to use. (A notable exception as of this writing is Bank of America - way to go, BofA!)
If you have this option available, you should definitely use it for as many important websites as you can (and have a backup key, just in case you lose one!) But what if you can't use that?
For most accounts, the best second factor available is an app that generates time-based one-time PIN (TOTP) codes for multiple websites at a time.
The best alternative - TOTP Apps
Google Authenticator and Authy are popular examples of these time-based OTP apps, and there are open-source solutions as well, like Aegis Authenticator. They can store a nearly unlimited number of accounts in one app.
Here's how it works: when you're setting up 2FA on your account, the website will provide you with a seed code along with metadata including the site and your username. This is normally provided in the form of a QR code that you can scan into the app for ease.
Then, whenever you log into your account, the site will challenge you to enter the code displayed in your app for that account. Since it is time-based, the code changes every 30 seconds to 1 minute and an expired or previously used one can never be used again. That way, even if you're unlucky enough to fall victim to the aforementioned keylogger, it will be much more difficult for a hacker to get into your account without your phone (unless your authenticator account is backed up online...).
These are still vulnerable to social engineering attacks on you, but as long as you're vigilant and never provide the code to a human, they're a pretty solid choice. Use them for any website that offers it, like banks, social media, email, Paypal, Amazon, etc.
The sad truth: The weakest link
So, you've read this far and decided you are going to set up 2FA on all of your online accounts. You've even downloaded Aegis or Authy and have already looked it over. You're all set to be 100% secure with a fully out-of-band second factor, right?
[Sigh]. Not always...
The sad truth is that many companies, although they offer one or more of these types of out-of-band authentication methods, will happily let you (or our friend the hacker) bypass them by using a less secure, and frequently in-band backup method. Being able to utilize the weakest link completely renders all you've done to secure your account absolutely useless.
This is done mainly for customer convenience, and for Customer Service department cost-savings. Using our out-of-band methods here is not really going to get you anywhere. But hopefully the future will bring better adoption of the more secure methods we've discussed, and provide a brighter outlook for online security.
Here is a great resource for finding out which companies support which types of 2FA